Advance-Fee Loan Release Scam
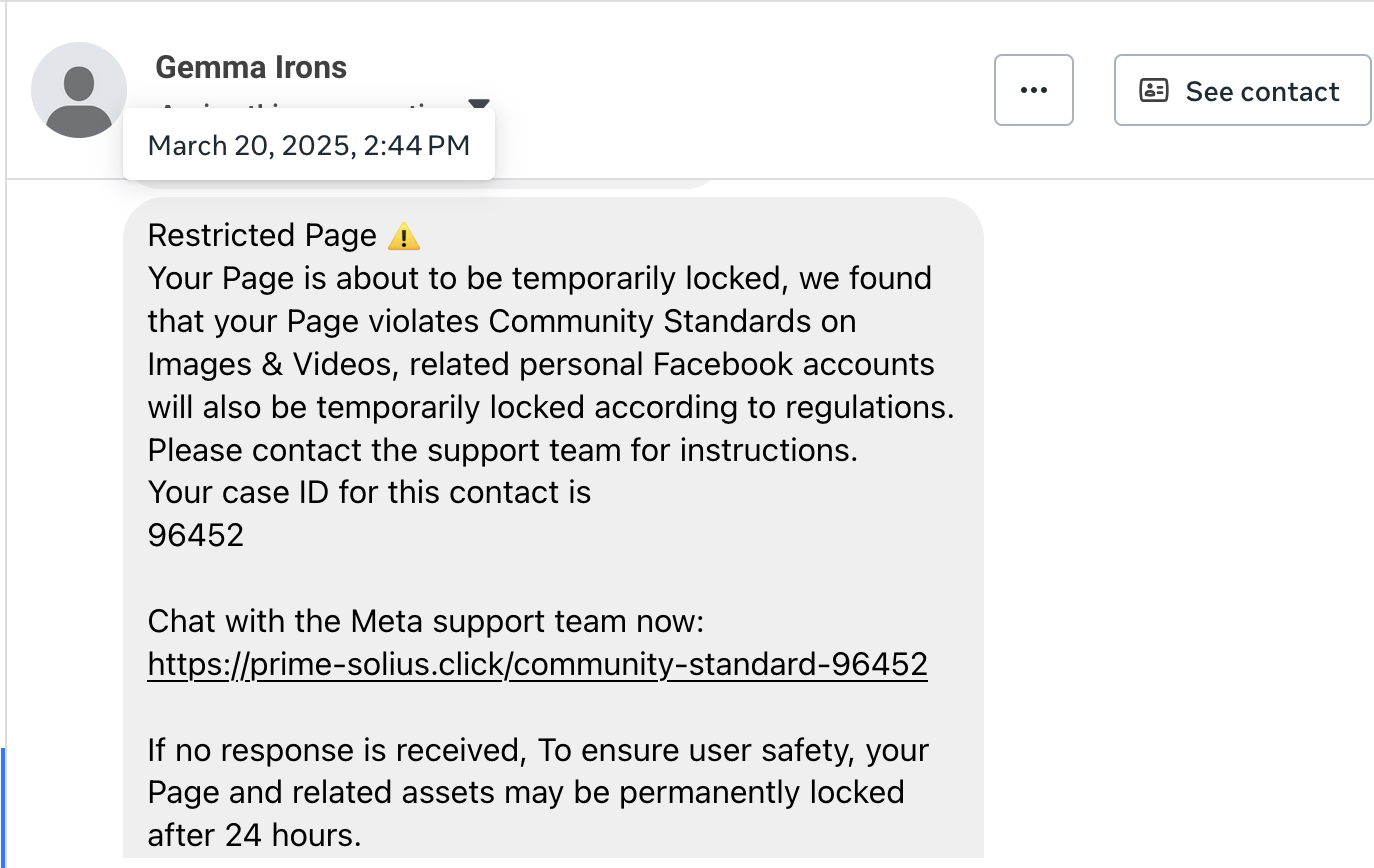
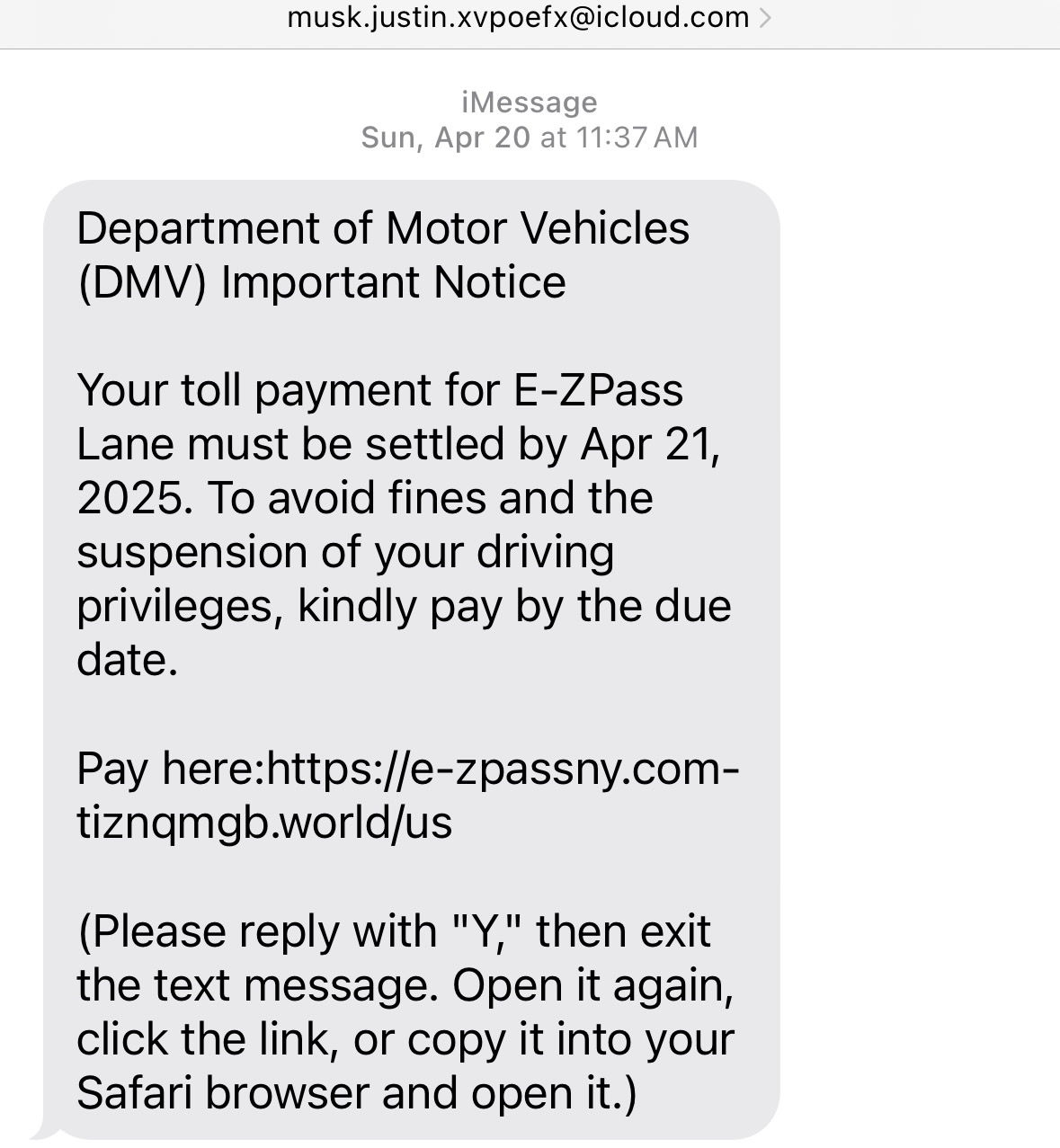
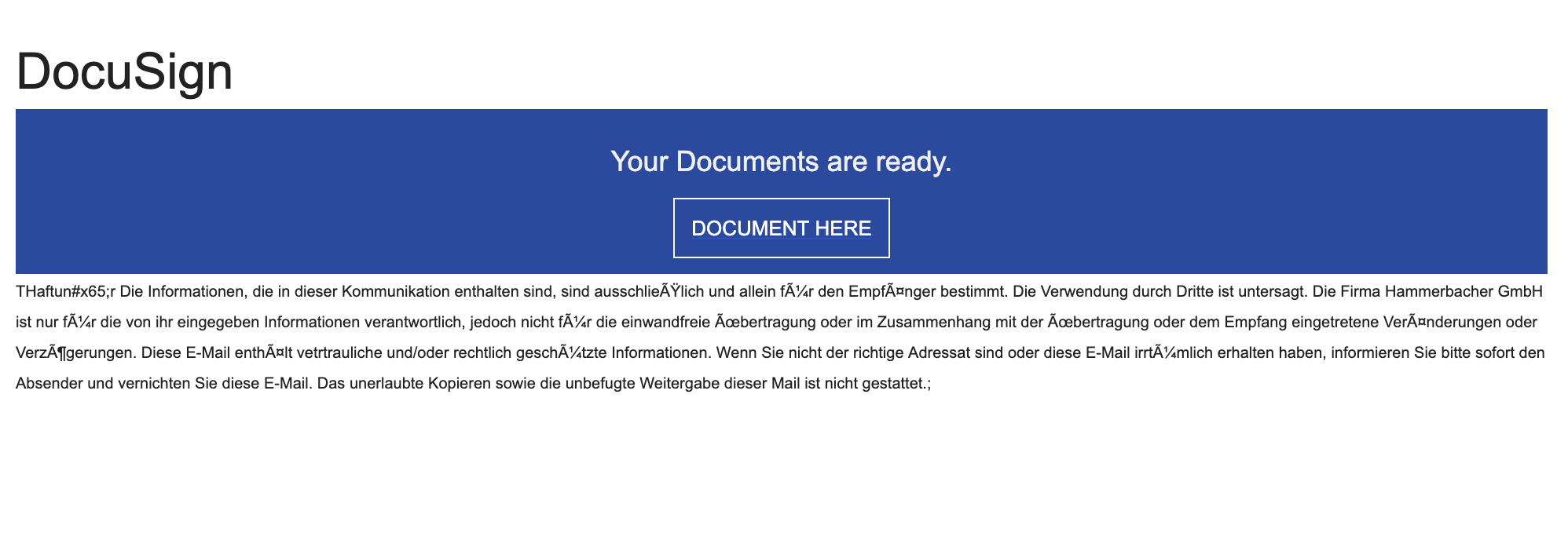
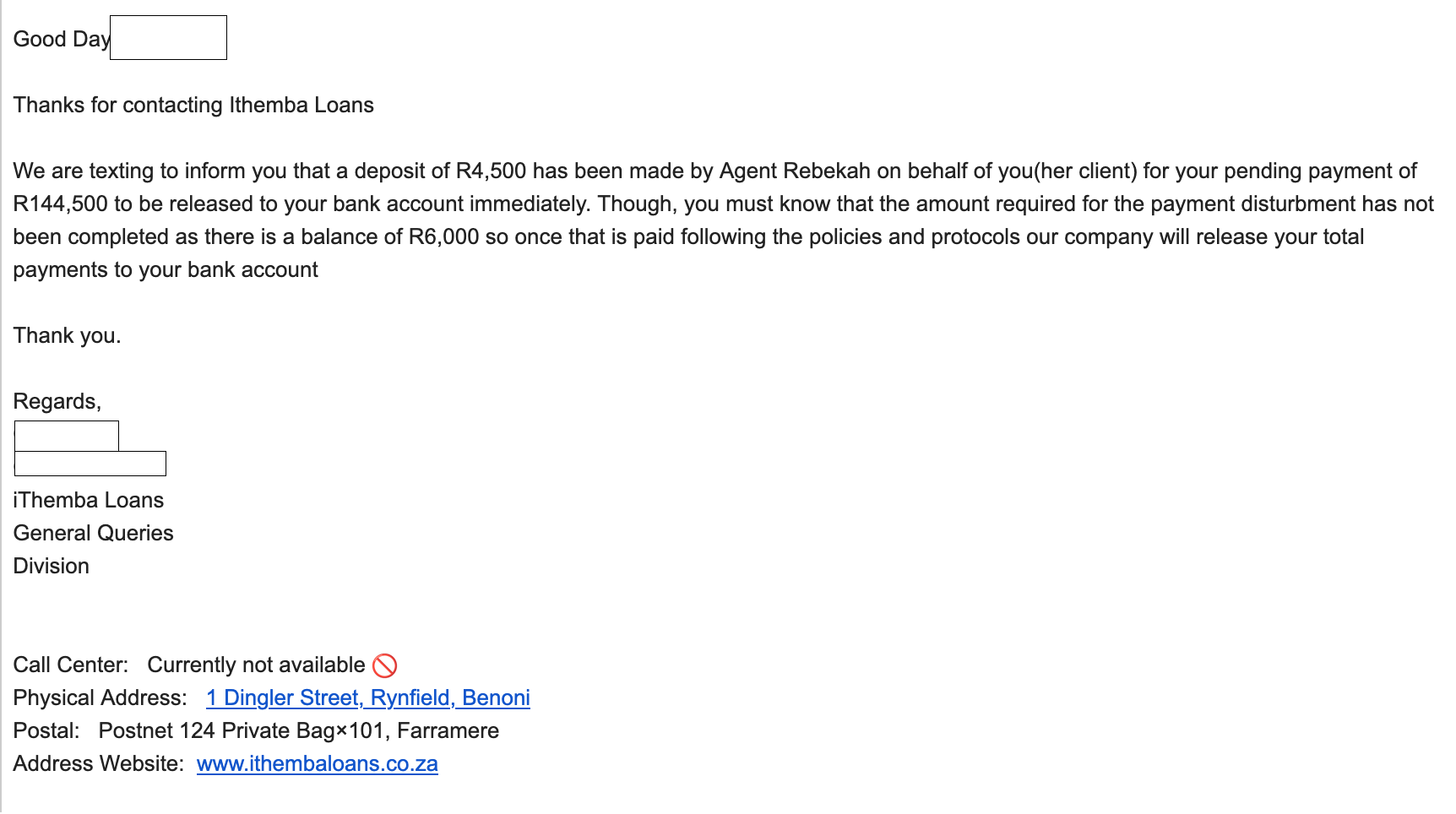
You’re told that a loan, payout, or “approved payment” is ready and will be sent to your bank “immediately” — but first you must pay a smaller fee (often called a release, processing, clearance, or compliance fee). Once you pay, the scammers either ask for more money because of “new problems,” or they disappear. No money is ever released.